IOCs
Domain
songtrustppc[.]com
URLwork[.]songtrustppc[.]com/login
Telegramt[.]me/SONGTRUST_01
SMS numbers likely rotating VoIP+1 (415) 529-0196,+1 (213) 548-9457
TL;DR
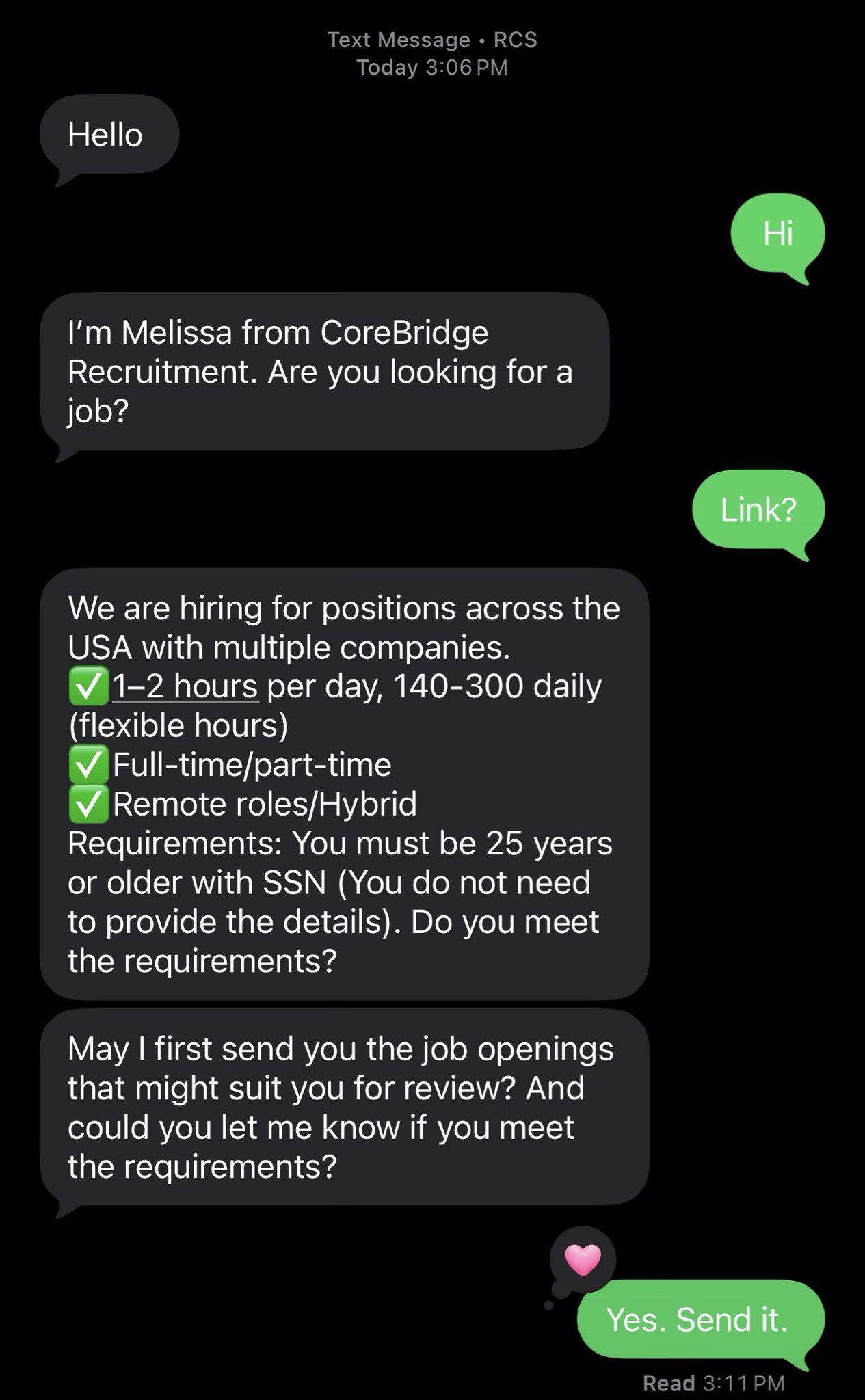
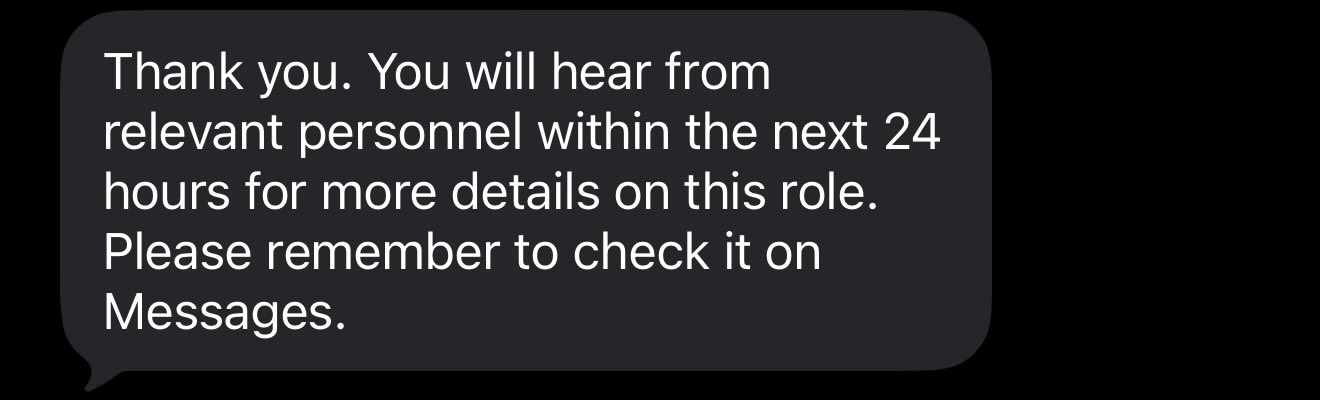
I got unsolicited SMS messages claiming to be from CoreBridge Recruitment, offering remote roles with unusually high pay for minimal work. After engaging, I was sent to a Songtrust branded login page that did not authenticate users. Clicking Sign in just redirected me to Telegram, where the scam moves to manual chat.
1) SMS lure
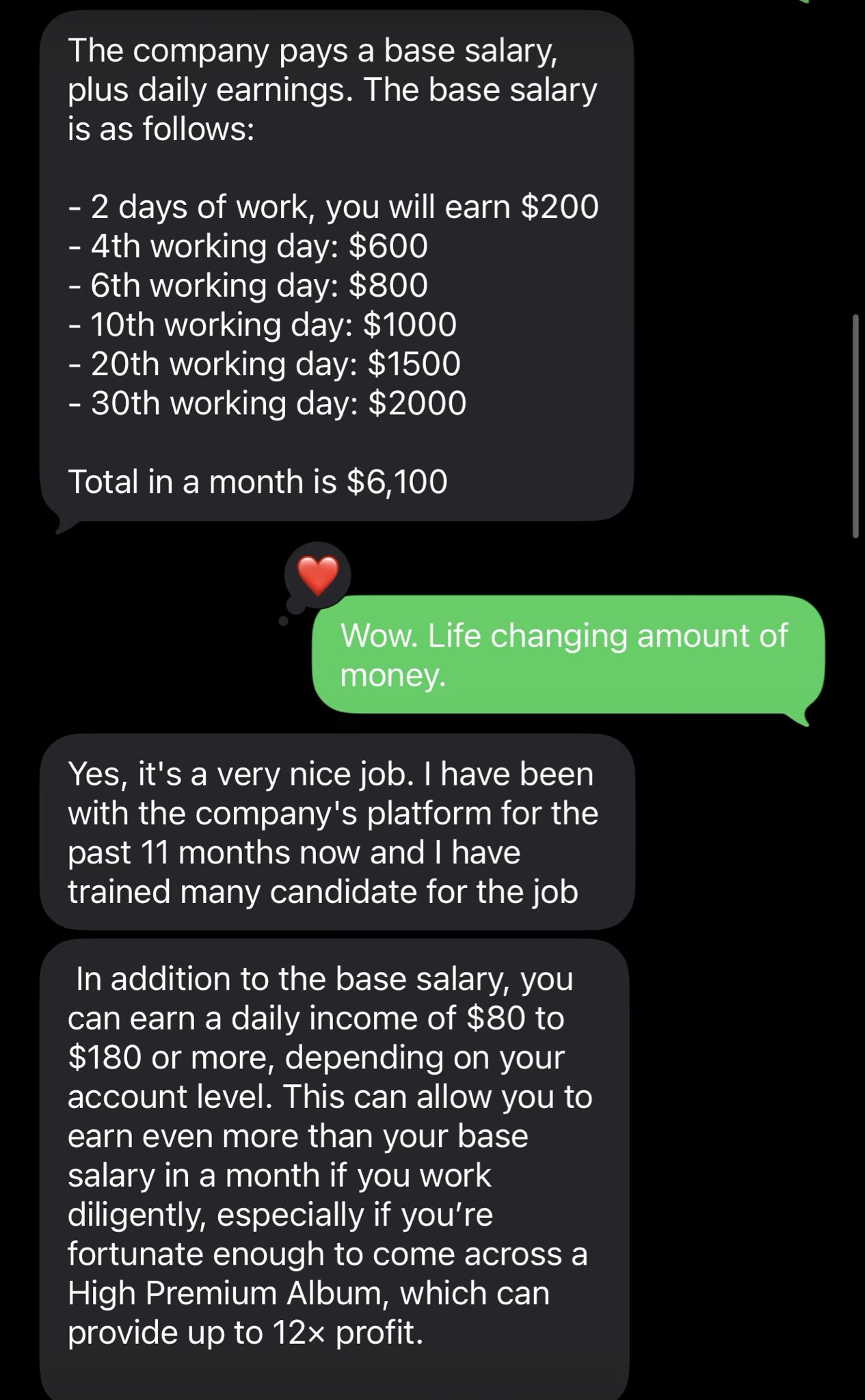
The pitch was classic. Low effort, high pay, and generic eligibility checks.
2) Fake Songtrust “portal”
The link pointed to:
work[.]songtrustppc[.]com/login
The page uses Songtrust branding and marketing language instead of an actual authentication form.
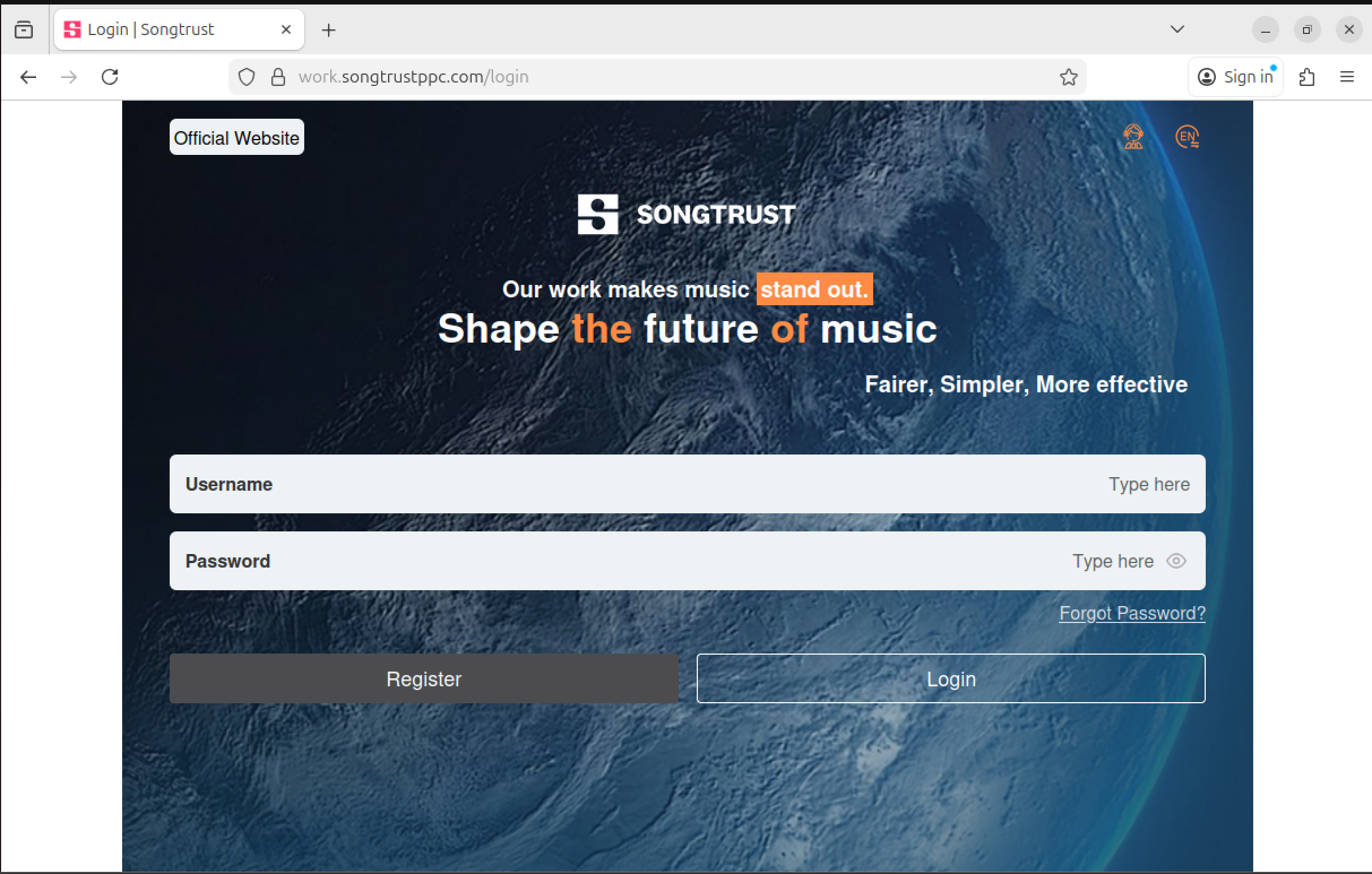
Static inspection
- No visible login form
- No backend auth endpoints referenced
- No credential submission on page load
The /login path is misleading and functions as a landing page, not an auth page.
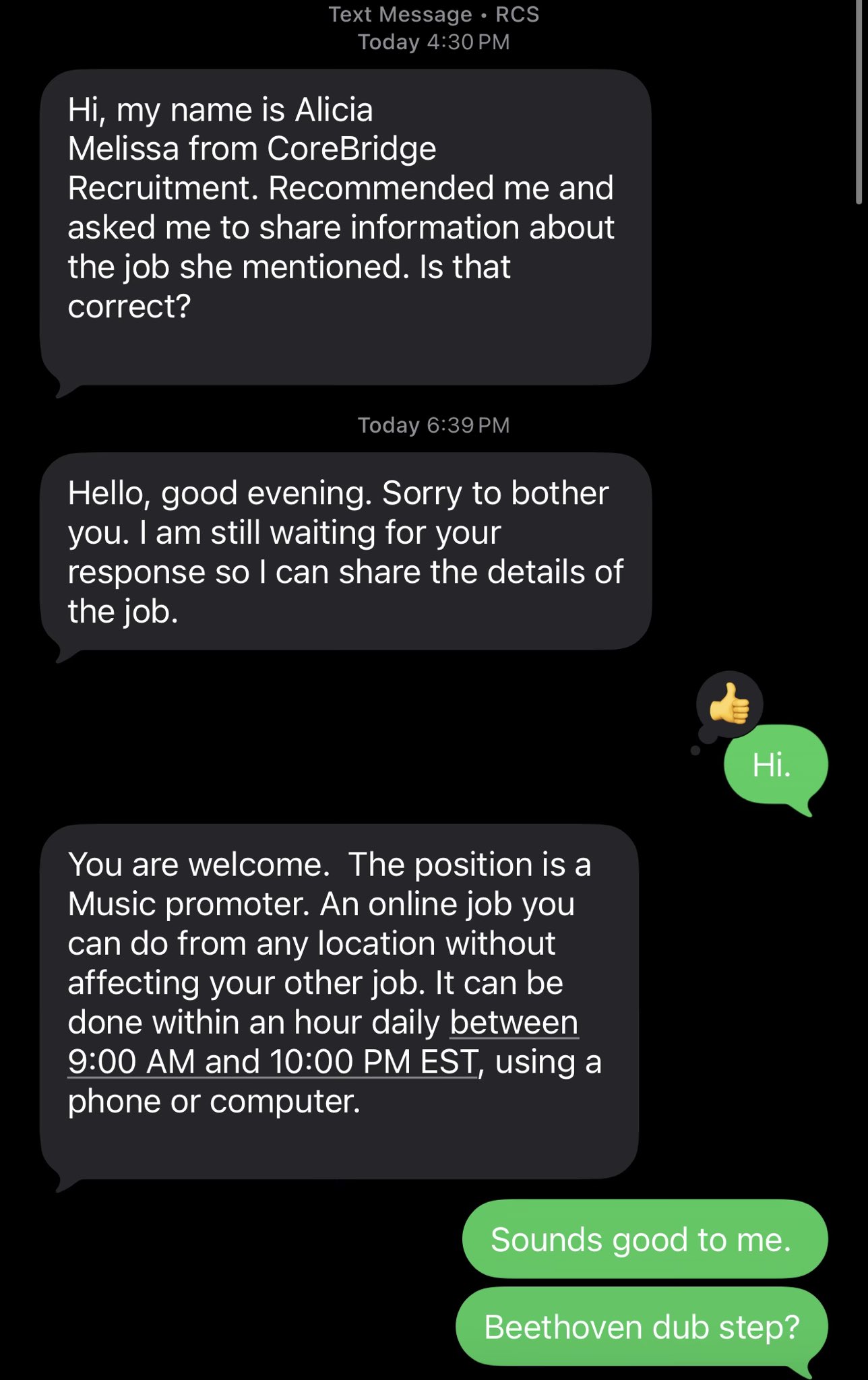
3) Redirect to Telegram
Clicking Sign in does not authenticate the user. It redirects to Telegram.
t[.]me/SONGTRUST_01
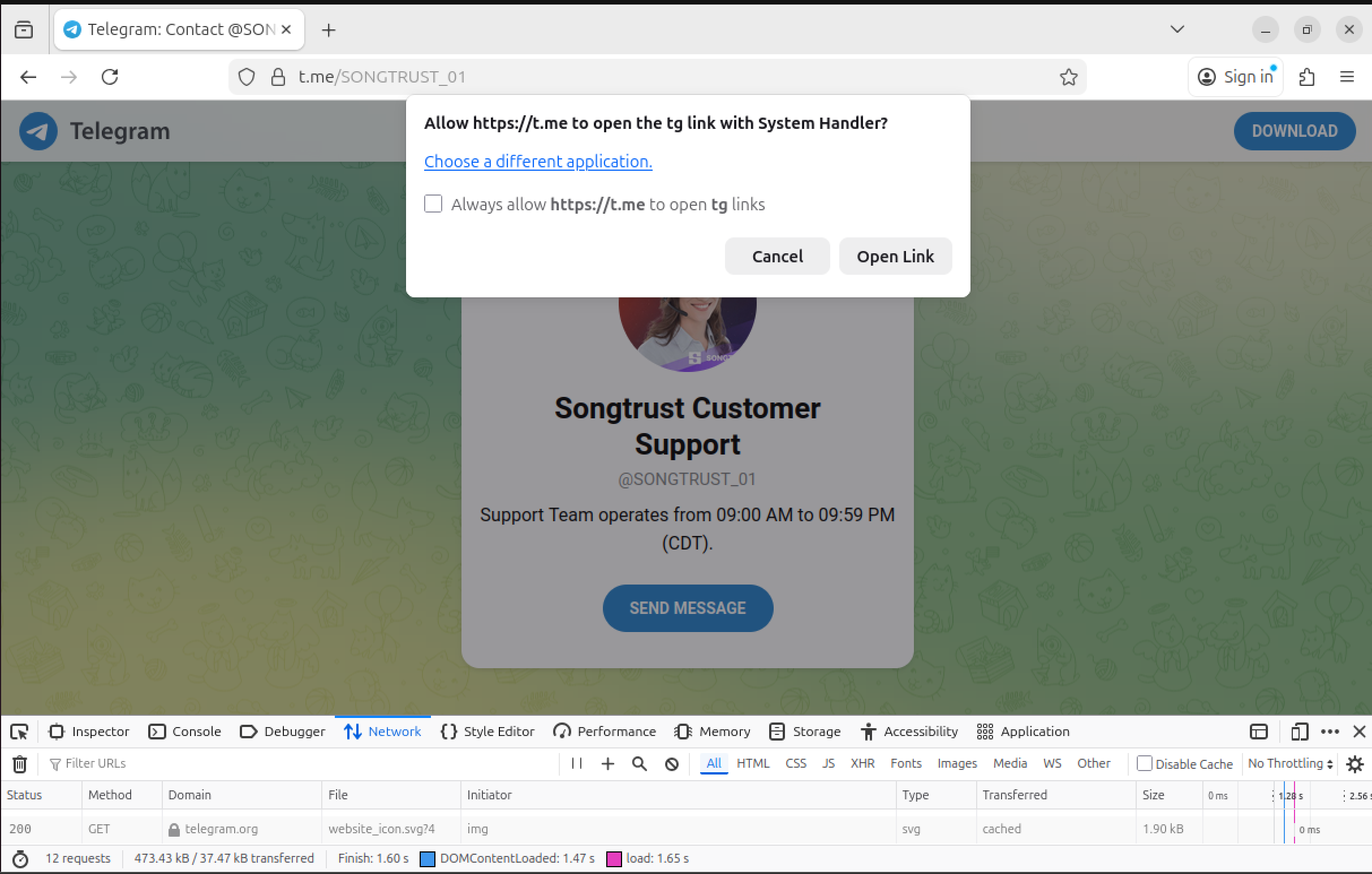
This confirms the site’s role as a traffic funnel. All meaningful interaction moves off platform to Telegram, where the scam is handled manually with screenshots, instructions, and next steps.
What this campaign relies on
- Brand impersonation using Songtrust
- Social engineering via SMS
- Off platform migration to Telegram
- Human in the loop fraud
No malware, payloads, or credential harvesting endpoints were observed.
Takeaway
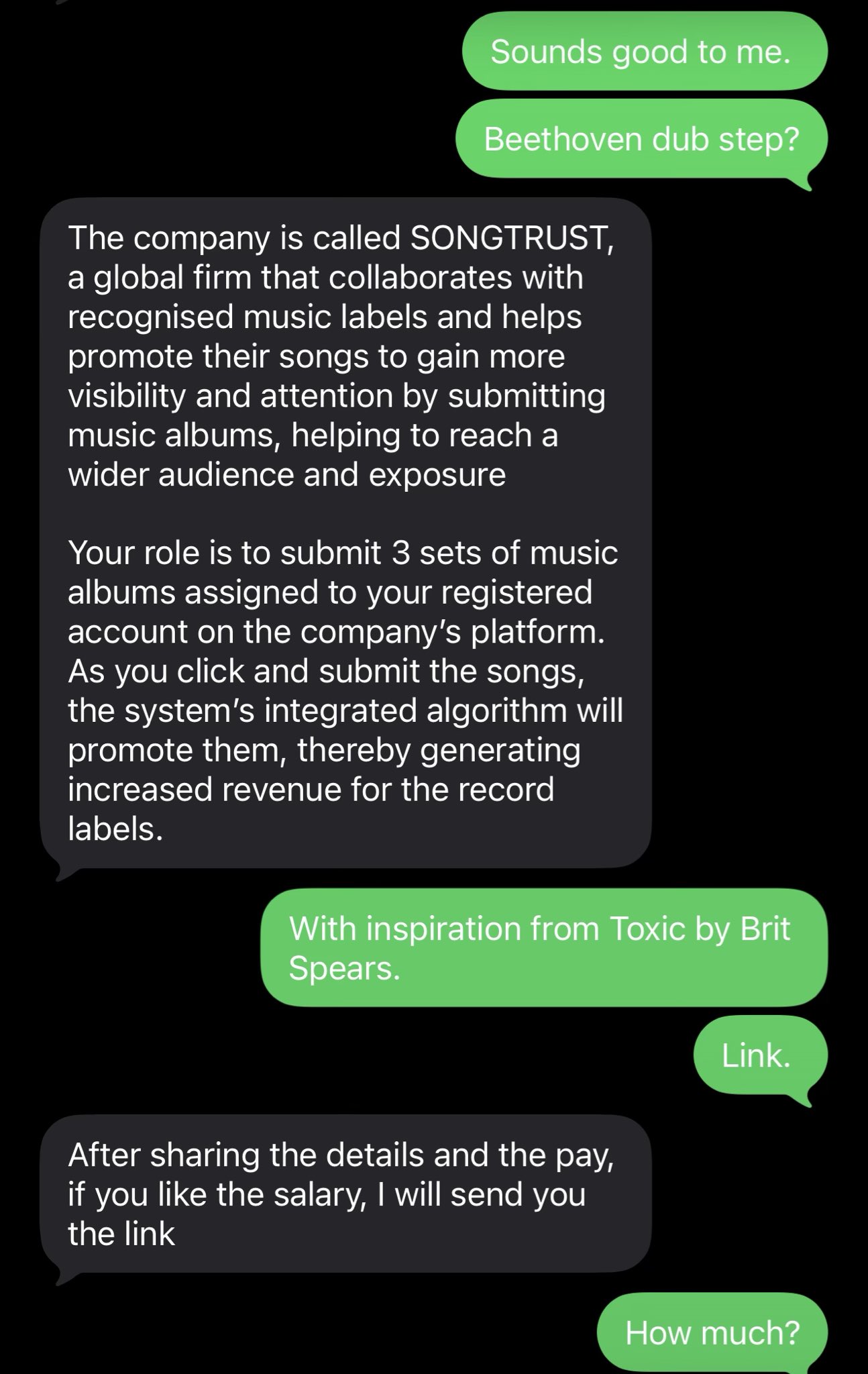
This was clearly a scam from the first message. The pitch was vague, the pay unrealistic, and the outreach unsolicited. I continued the conversation intentionally — not because it was convincing, but to observe how the flow worked. When I pushed back (asking about a sign-on bonus), the tone immediately shifted to defensiveness and gaslighting, a common tactic used to reassert legitimacy and keep victims engaged.
The site itself did nothing malicious. Its only purpose was to redirect the conversation to Telegram, where the scam is executed manually.